Sabancı University
Biometric cryptosystems combine cryptography and biometrics to benefit from the strengths of both fields. In such systems, while cryptography provides high and adjustable security levels, biometrics brings in non-repudiation and eliminates the need to remember passwords or to carry tokens etc.
Recent research has focused on combining cryptography and biometrics to take advantage of the benefits of both fields [2][3][4][5][6]. While biometrics provide non-repudiation and convenience, traditional cryptography provides adjustable levels of security and can be used not just for authentication, but also for encryption. Uludag et al. makes the distinction between two general approaches within what they call crypto-biometric systems, according to the coupling level of cryptography and biometrics [7]: Biometrics-based key release refers to the use of biometric authentication to release a previously stored cryptographic key. Biometric authentication is used as a wrapper, adding convenience to traditional cryptography where the user would have been in charge of remembering his/her key; however the two techniques are only loosely coupled. Biometrics-based key generation refers to extracting/generating a cryptographic key from a biometric template or construct. In this case, biometrics and cryptography are tightly coupled: the secret key is bound to the biometric information and the biometric template is not stored in plain form.
The difficulty in biometric cryptosystems comes from the fact that biometric measurements are variable and noisy: the same biometric may change between consecutive acquisitions (due to injury, ageing, even mood etc.) and noise can be introduced to a biometric signal by an acquisition device or the environment. While it would be very convenient to use biometric traits for encryption, for instance someone using his fingerprint or handwritten signature to encrypt a document and securely send it over public network, this is very difficult due to the aforementioned variability of the biometric signals and the fact that encryption and decryption operations cannot tolerate the perturbation of even a single bit. In its most basic sense, generating a cryptographic key directly from a biometric trait, for instance fingerprints, has not been very successful, as it involves obtaining an exact key from a highly variable data. For instance Feng andWah has only been able to generate a 40-bit private key from online signatures with an 8% equal error rate (the key extracted from a genuine signature is not correct or a forgery successfully extracts the key) [1].
According to the above definition, recent work of Juels et al. [2] and Tuyls et al. [3] are classified as biometrics-based key generation, as they require a tight coupling of cryptography and biometrics. In particular, the fuzzy vault construct of Juels et al. forms the basis of this paper. Jules and Wattenberg proposed the fuzzy commitment scheme [8]; later Juels and Sudan extended it to the fuzzy vault scheme [2] and described how it can be used to construct/release an encryption key using one's biometrics: a secret (cryptographic key) is "locked" using a biometric data of a person such that someone who possesses a substantial amount of the locking elements (e.g. another reading of the same biometric) would be able to decrypt the secret. Note that the fuzzy vault scheme is classified as a key-generation scheme in Uludag et al., because of its tight coupling of cryptography and biometrics [7]. However, in the sense that the biometric data releases a previously stored key, it can also be seen as a releasing mechanism.
Our work below demonstrates how to hide a secret into a fuzzy vault, so as to be released with an online signature.
--------------------------------------------------------------------------------------------------------------------------------------------------------------
Biometric Cryptosystem Using Online Signatures
"Biometric Cryptosystem Using Online Signatures", A. Kholmatov and B. Yanikoglu, The 21st International Symposium on Computer and Information Sciences November 1-3, 2006 - Istanbul, Turkey
In this work, we present a biometric cryptosystem which uses online signatures, based on the fuzzy vault scheme of Jules et al. The fuzzy vault scheme releases a previously stored key when the biometric data presented for verification matches the previously stored template hidden in a vault. The online signature of a person is a behavioral biometric which is widely accepted as the formal way of approving documents, bank transactions, etc. As such, biometric-based key release using online signatures may have many application areas. We extract minutiae points (trajectory crossings, endings and points of high curvature) from online signatures and use those during the locking & unlocking phases of the vault. We present our preliminary results and demonstrate that high security level (128 bit encryption key length) can be achieved using online signatures.
A Sample Signature (top) and it's marked minutiae poins (bottom)

Fuzzy Vault: Locking Phase
|
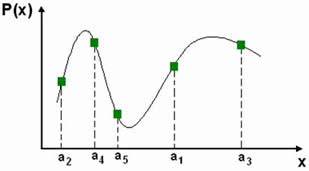 |
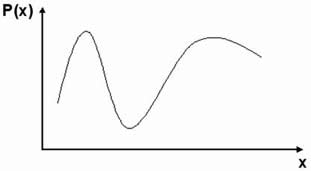
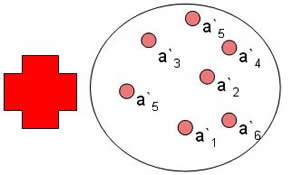
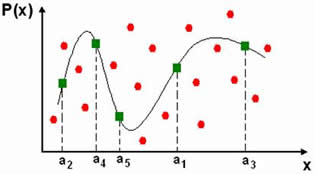
| (1) Create a polynomial by encoding a Key to a polynomial's coefficients | (2) Project locking elements on to the polynomial, ai denotes i'th element |
 |
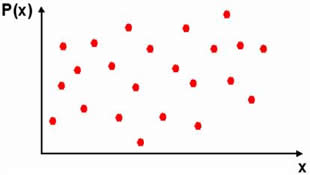 |
| (3) Randomly create & add chaff points (represented by red dots) | (4) Final appearence of the Vault, as stored to the system's database |
Fuzzy Vault: Unlocking Phase
|
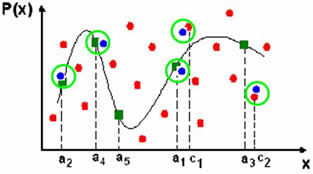
| (1) Fuzzy Vault of claimed ID (left) and test unlocking set (right) |
|
| (2) Test unlocking set matched against the vault. Matched vault and test points are circled in green. Polynoial reconstraction is performed using only these matching points. |
for details refer to:
."Biometric Cryptosystem Using Online Signatures", A. Kholmatov and B. Yanikoglu, The 21st International Symposium on Computer and Information Sciences November 1-3, 2006 - Istanbul, Turkey
------------------------------------------------------------------------------------------------------------------------------------------------------------
Our other work in this area implements the fuzzy vault with fingerprints, and adds secret sharing capabilities to it:
Secret Sharing Using Biometric Traits
In biometric based authentication, biometric traits of a person are matched against his/her stored biometric profile and access is granted if there is sufficient match. However, there are other access scenarios, which require participation of multiple previously registered users for a successful authentication or to get an access grant for a certain entity. For instance, there are cryptographic constructs generally known as secret sharing schemes, where a secret is split into shares and distributed amongst participants in such a way that it is reconstructed/ revealed only when the necessary number of share holders come together. The revealed secret can then be used for encryption or authentication (if the revealed key is verified against the previously registered value).
In this work we propose a method for the biometric based secret sharing. Instead of splitting a secret amongst participants, as is done in cryptography, a single biometric construct is created using the biometric traits of the participants. During authentication, a valid cryptographic key is released out of the construct when the required number of genuine participants present their biometric traits.
for details refer to:
"Secret sharing using biometric traits", A. Kholmatov, B. A. Yanikoglu, E. Savas, A. Levi, Biometric Technology For Human Identification III, 18 April 2006, Orlando, Florida USA, In Proceedings of SPIE Vol. #6202